Maintaining one's privacy and security when using the internet is more important than it has ever been in this day and age.
Proxy servers are one of the techniques that may be utilized to assist with this matter.
To be more specific, what precisely is a proxy server, and how does it function? In this article, we offer an explanation of how proxy servers function as well as the advantages that they offer.
What Is a Proxy Server?
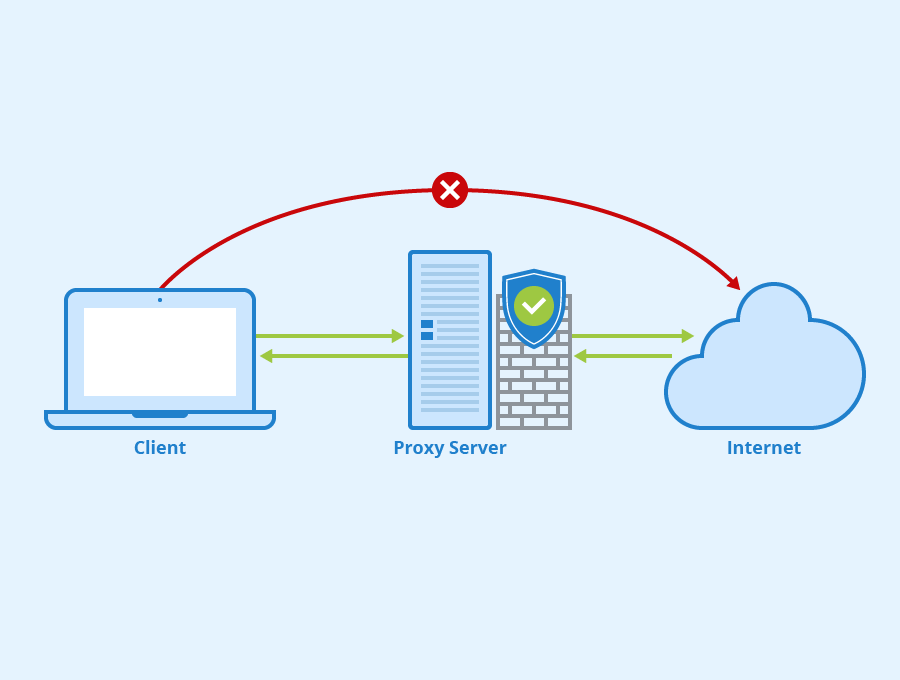
A proxy server acts as an intermediary between users and the internet, sometimes in the form of a router or system. As a result, it facilitates the defence of private networks against cyberattacks.
Servers like this are known as "intermediaries" because they mediate communication between users and the websites they access.
A computer's IP address is what allows it to connect to the internet. Like your home's street address, this specifies the destination of incoming data and the return address of outgoing data so that other devices may verify its authenticity.
Just like any other computer on the internet, a proxy server has its own unique IP address.
How Does a Proxy Server Work?
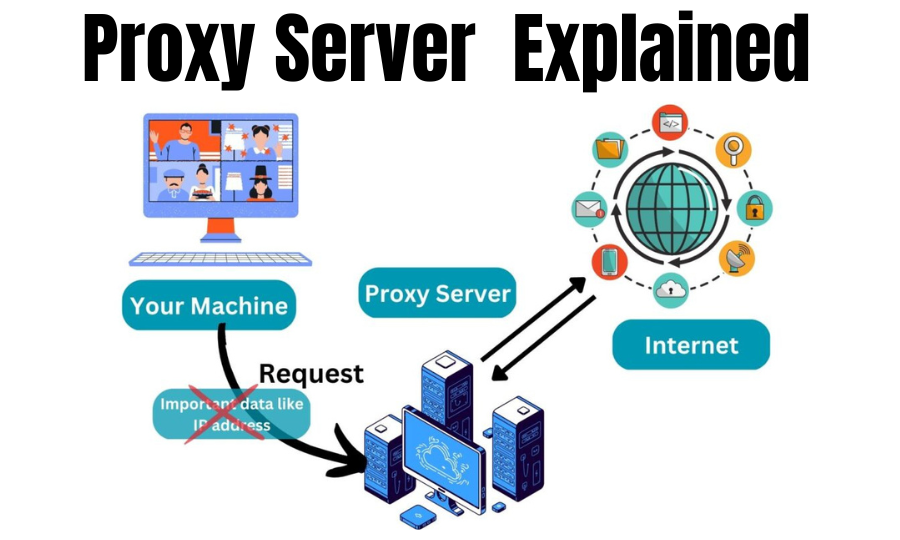
For your internet inquiries, a proxy server receives and evaluates the results before returning them. The proxy server is the only link between your device's local network and the websites you're viewing.
Each proxy server uses your computer's IP address. Your computer or device's IP address is its home address.
Internet queries are routed back to your IP address, like mail is forwarded to your home address, ensuring data is transmitted to the right location.
Your IP address is visible to web servers and those without a proxy. Your IP address is easy to find, putting you at risk for identity theft and other security breaches.
An internet proxy has an IP address to avoid requiring your genuine IP address.
How to Get a Proxy
Both software and hardware versions are available. In order to receive, transmit, and forward data from the web, your network needs hardware connections, which lie between your network and the internet.
A provider or the cloud is the usual location for software proxies. A program that allows you to communicate with the proxy may be downloaded and installed on your computer.
A software proxy is usually available for a monthly price. They can be free at times.
A business with a large number of devices may need a paid proxy service, as free versions sometimes provide fewer addresses and may only cover a small number of devices.
Types of Proxy Servers
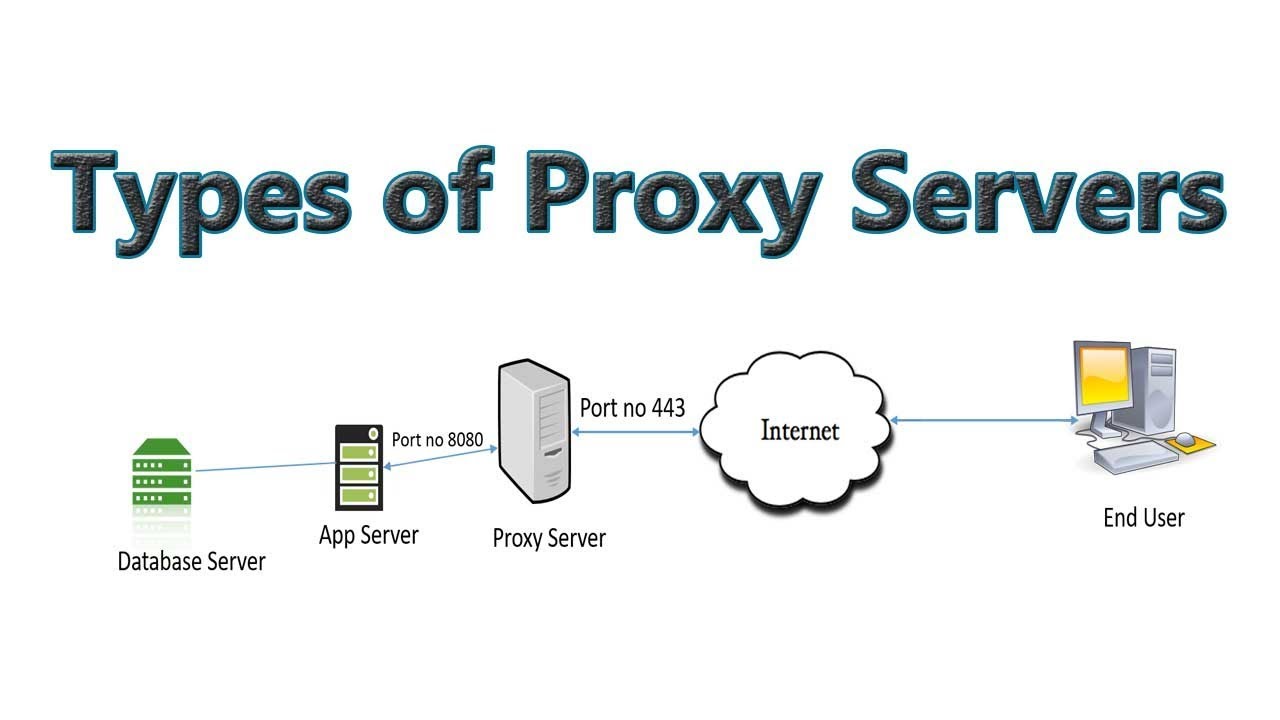
There are various ways that proxy services can be used. It's important to know exactly what the proxy server does for you and make sure it works for your needs.
Transparent Proxy
While a transparent proxy conceals its identity as a proxy server from websites, it continues to transmit your IP address, which is used to identify you to the web server.
Because of how simple they are to set up on both the client and server side, transparent proxies are commonly used for content filtering in schools, public libraries, and businesses.
Anonymous Proxy
Anonymous proxies will tell websites that they are proxies, but they won't give out your IP address. This helps protect your privacy and stop identity theft. They can also stop a website from showing you marketing material that is specific to your area.
Distorting proxy
A proxy server that produces a false IP address for you while claiming to be a proxy is known as a distorting proxy. This works like the anonymous proxy, but by giving a fake IP address, you can make it look like you're from a different place to get around content limits.
High Anonymity proxy
Sometimes, high anonymity proxy services change the IP address they give to the web server. This makes it hard to tell who is sending what data. The safest and most private way to browse the web is through high privacy proxies.
Benefits of Proxy Servers
Despite their apparent simplicity, proxy servers provide substantial benefits to businesses and information technology companies. Proxy servers have many uses and advantages, some of which are listed here.
Improved Security
Data breaches are costly and can cause large losses, which is why proxy servers are used by corporations primarily.
A proxy server can offer another degree of protection by preventing harmful internet traffic from reaching the company's servers.
Proxy servers may not be able to prevent all hacking attempts on a company's network, but they can increase system security and decrease the likelihood of intrusions.
Anonymity
The internet cannot determine the IP address of the requesting business because proxies are placed between the two networks.
The success of a business depends on its research and development process, which is an important aspect of its intellectual property.
An extra safeguard prevents the theft of important corporate data by separating the unfiltered internet from the organization's servers.
Faster Speed
Proxy servers also provide the crucial role of caching, which allows for faster performance. Proxy servers can save frequently used websites in their cache, so they don't have to constantly query the internet for new requests to those pages.
On top of that, proxy servers often remove advertisements from websites and compress information, which further speeds up the internet.
Control Internet Usage
Unwanted content can be blocked via proxies. For instance, in order to prevent employees from being distracted from their job, some firms may choose to restrict specific social networking sites.
Network administrators can also use a proxy server to keep an eye on all internet requests to make sure nothing shady is happening.
Avoiding Limitations
Access to specific websites may be restricted based on IP address. Using a proxy server allows businesses to circumvent geo-restrictions on content access, allowing employees to view websites that are otherwise inaccessible.
Conclusion
A proxy server is a useful tool that acts as a go-between for people and the internet. This is only one layer of protection, but it can help stop hackers from getting into private networks and safeguard personal computers from viruses and other dangers.



Leave a Reply