While proxy and Reverse Proxy are both types of intermediaries that manage and redirect traffic inside a network,
proxy servers differ in their operational structure and the way they handle traffic in one direction compared to the other.
Understanding the distinctions between forward and reverse proxies and their roles in system architecture is crucial.
This knowledge empowers you to make informed decisions and optimize your network's performance.
What Is a Proxy (Forward Proxy)

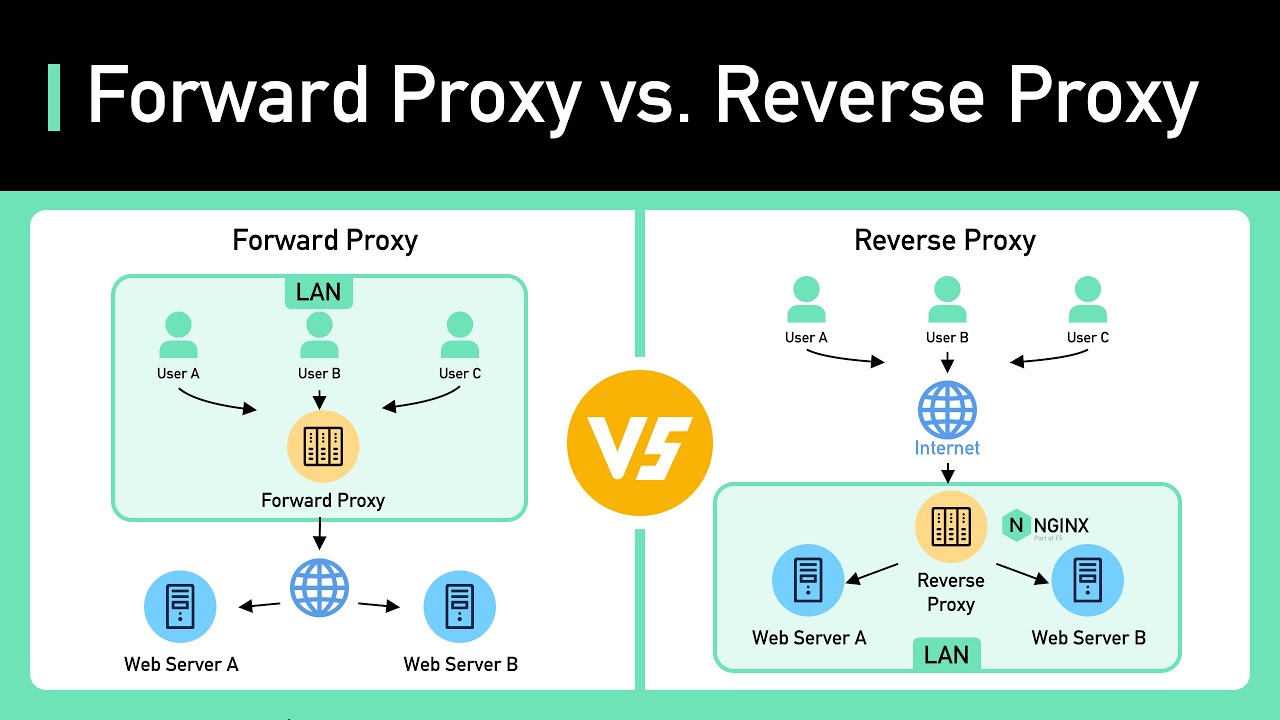
A proxy server, which is also called a forward proxy, is a server that sends data between a client or clients and another system, usually one that is not on the same network.
In this way, it can control traffic based on rules that have already been set, change and hide client IP addresses, apply security protocols, and stop traffic it doesn't know about.
Proxy servers are often used in business settings and data centres where networks are shared.
They give clients a single interface to use, so they don't have to implement all of their own rules and route control logic.
Types of Forward Proxies
Their location or the places they serve primarily to distinguish between the several essential types of forward proxies.
Residential proxy
Most residential proxies are provided by an Internet Service Provider (ISP) and hide the user's address.
Users may choose a specific region, like a nation or city, and it will seem like they're from that area because the residential proxy address has an actual physical location.
Datacenter proxy
This type of proxy is ordinarily used by a business, not an ISP. Virtual private networks (VPNs) housed inside data centres can assign IP addresses using their own address pool or that of other cloud providers.
Mobile proxy
Although the name suggests that a mobile proxy is designed for mobile devices, in reality, the proxy IP address originates from a mobile network, as opposed to a residential or data centre proxy, which are called after their fixed point of origin.
On the other hand, a mobile proxy can trick users into thinking their device is connected to a mobile data network even though it doesn't have one.
Criminals who engage in online fraud frequently employ mobile proxies.
What Is a Reverse Proxy?

A reverse proxy is a server that resides between several web servers and the Internet, acting as an intermediary between the servers and the users.
After receiving the request, the reverse proxy forwards it to the client's desired internet resource.
The reverse proxy is responsible for receiving responses from web servers after they have sent requests to them. After that, the reverse proxy gives the answer back to the client.
Types of Reverse Proxies
Most reverse proxies work the same way. However, there are two main kinds of reverse proxies that can be told apart by their work. Simply put, they are load balancers and reverse proxies.
Regular reverse proxies
This kind of proxy takes a client's request, sends it to the server for processing, and then returns it to the client. It is mostly used for safety reasons.
Load balancers
This type of proxy is a reverse proxy that goes to multiple server instances. It can split up the traffic among several other computers and handle client-server interactions between all of them.
This type is better designed to spread the work across multiple computers, which speeds things up and improves performance.
Similarities Between Proxy and Reverse Proxy
When protecting devices connected to a private network from dangers from the Internet and other external networks, the most significant similarity between a forward proxy and a reverse proxy is that they both provide this protection.
You can restrict the types and amounts of files that go through both forward and reverse proxies. They can also stop users who have yet to be verified from sending requests through them.
Port and protocol swapping is something that both forward and reverse proxies can do. This can make it even harder to figure out how to access resources hidden behind them.
Another possibility is that the same software can be used to configure both a forward proxy and a reverse proxy.
Differences Between Proxy and Reverse Proxy
A forward proxy handles client data and ensures its safety and security. On the other hand, a reverse proxy protects servers by handling client requests, ensuring they reach the right server, and then sending the results back to clients without them knowing that the server was directly involved.
In other words, the significant difference between a forward proxy and a reverse proxy is what they do and which way data flows.
A forward proxy, sometimes called a proxy server, controls data between clients and outside systems by hiding client IP addresses and applying security rules.
In contrast, a reverse proxy sits between clients and servers and protects servers by taking client requests, sending them to the correct server, and then sending the results back to the client.
The reverse proxy handles communication and looks like the only point of contact to the client, so unlike a forward proxy, the client doesn't know that its request was sent to another server.
Can a Forward Proxy Act as a Reverse Proxy?
A forward proxy server cannot function as a reverse proxy server. Although these proxies may share similar concepts, they serve entirely different purposes.
A proxy is not just an IP address alone. Proxies consist of IP addresses and specialized software that enables them to function as intended.
Forward and reverse proxies have distinct software designed for their specific tasks. This is why forward proxies cannot be used as reverse proxies.
Conclusion
To sum up, both forward and backward proxies are essential parts of current network architectures, but they do different things and have different abilities.
Forward proxies play a crucial role in managing and securing client-side traffic, providing a reassuring layer of protection for your network.
By understanding the differences between forward and reverse proxies, you can design reliable, efficient, and secure systems that meet the needs of modern services and applications.
This knowledge should motivate you to delve deeper into this important aspect of network architecture.
Continue reading; GoLogin Anti Detect Browser - The Best Way to Make Multiple Clients



Leave a Reply